Table of Contents
Security Economics
Themes
Among the research topics of the Security Group the main stream of this research topic is to understand the various economic trade-offs that attackers and defenders face, and (possibly) derive some conclusions that policy makers and individual citizens can take to be more protected.
- On the fairness of seucirty taxes in presence on interdependence
- Estimating quantitative likelihood
- Cyber-Insurance: good for your company, bad for your country?
- The Work Averse Attacker Model (A different way to consider attackers)
- Black markets actually work!
- Risk vs Rule base regulation: what is the best way to regulate?
- The security cost of using free and open source components in proprietary products
- Is “more security training” always an effective solution? Turkey's case study
See also our section on Finding and Assessing Vulnerabilities in particular if you are interesting in understanding what's the risk reduction for different types of vulnerabilities and Malware Analysis.
Beyond 1-5 Risk Matrices: estimating quantitative attack success likelihood from data
Several definitions of risk exist (probability and impact, uncertainty and expected consequence, etc.) but at the end of the day they all ultimately collapse to the intuitive relation
- Risk = Impact · Likelihood
For a company, impact is easy to calculate as data about one's own asset is routinely collected. Likelihood is stillthe holy grail. So, both ISO/27001 and NIST 800-30 standards suggest the use of risk matrices as a tool to support such decisions. So you get a 5×5 risk matrix, where the interaction between the rare, frequent, …, certain likelihood levels and the minor, severe, …, critical consequence levels results in a final 5-level risk evaluation from low to high. This is pretty rough and well known to be full of errors.
In our Risk Analysis paper we show that it is possible to compute a quantitative estimation of the success of attack likelihood. Our measure is generated by technical data that all medium-large organizations already have in their infrastructure: vulnerability assessment tools are mandated to most firms processing credit cards, and periodic auditing for compliance requires VA reports to be handed to the assessor. Similarly, IDS and Firewall technologies are widely adopted.
This data is currently often used in an unstructured way to either generate automatic reports on vulnerability severity, or to try to traceback known incidents. Our methodology proposes to correlate this data to measure on one side the exposure of a system to potential attacks, and on the other the opportunities that a successful attack has to breach a vulnerable system and escalate to the infrastructure. By enabling users in performing objective estimations of risk, our methodology makes a step forward toward the establishment of comparable measures for security
Cyber-Insurance: good for your company, bad for your country?
Our Cyber-insurance paper at the Workshop on Economics of Security 2017 shows that in spite of what Bruce Schenider and the US Congress think, cyber-insurance might be a bad idea.
'Cyberinsurance' is a broad industry term indicating a corporate liability insurance covering damages due to security breaches of the IT corporate infrastructure. It is a booming market that raises significant expectations: several policy makers (e.g. the UK Paymaster General and the US Senate Committee on Security), and several cyber experts (e.g. Bruce Schneier) have heralded it as a mechanism for efficiently valuing the cost of cyber attacks and to act as an effective substitute government action. Whilst the effect of purchasing insurance on the behavior of individuals or firms has been studied for more than four decades, the unique, adaptive feature of cyberinsurance have not been studied.
In our paper we show a very general model of heterogeneous firms, making risk averse decisions facing losses from cyber attacks conducted by strategic adversaries in a Cournot competition. There are essentially no assumtpions, except that attackers are wishing to make money, if opportunity arise and will not be very particular on the intended victims.
We demonstrate that whilst the presence of actuarially fair insurance increases the aggregate utility of target firms, the presence of insurance does not necessarily increase the security expenditures wrt those mandated by a benevolent social planner. Furthermore, we show that when insurance is provided by a monopolist insurer mandating firms security expenditure (as it has been proposed) the aggregate security expenditure is predicted to fall dramatically (and the number of attackers to increase).
In other words, people would rather pay for insurance and just deploy minimal security measures than invest in costly security measures. Firms will all be happier, and the country will end in mess. Delegating to cyberinsurers the policy maker role of regulating security expenditures might yield a digital tragedy of the commons.
The Work Averse Attacker Model
More than 30 years from the Dolev Yao model, and the all powerful attacker, it is time for a change! Our new WAAV Paper at the Workshop on Economics of Security 2017 proposes a new model of the attacker that is actually much closer to the empirical data.
A common conceit is that the typical cyber attacker is assumed to be all powerful and able to exploit all possible vulnerabilities with almost equal likelihood. We present, and empirically validate, a novel and more realistic attacker model borrowing from the economic theory by N. Stokey.
The intuition of our model is that a mass attacker will optimally choose whether to act and weaponize a new vulnerability, or keep using existing toolkits if there are enough vulnerable users.
The model predicts that mass attackers may
- exploit only one vulnerability per software version,
- include only vulnerabilities with low attack complexity, and
- be slow at introducing new vulnerabilities into their arsenal.
We empirically test these predictions by conducting a natural experiment for data collected on attacks against more than one million real systems by Symantec's WINE platform. Our analysis shows that mass attackers fixed costs are indeed significant and that substantial efficiency gains can be made by individuals and organizations by accounting for this effect.
The picture on the side (PDF) shows the fraction of systems receiving the same attack repeatedly in time (red, solid) compared to those receiving a second attack against a different vulnerability (black, dashed). The vertical line
indicates the number of days after the first attacks where it becomes more likely to receive an
attack against a new vulnerability rather than against an old one.  }}
}}
The second picture (PDF) shows the volume of received attacks as a function of time for the three types of attack. A1 is represented by a solid black line; A2 by a long-dashed red line; A3 by a dashed green line. The grey areas represent 95% confidence intervals. For Internet Explorer vulnerabilities the maximum T between two attacks is 1288 days; for SERVER is 1374 days; PROD 1411; PLUGIN 1428. This can be determined by the timing of first appearance of the attack in the WINE database.
If you like to have an idea of the model this other picture shows you the Change in the number of attacked systems for two attacks against different systems Δ = T days apart (PDF).
If you are interested in knowing whether we could use this insight for actual predictions please look at our vulnerability section where we report our work on risk reduction that made its way to the CVSS (Common Vulnerability Scoring System) v3 world standard.
The seconomics (security-economics) vulnerabilities of Decentralized Autonomous Organizations
Traditionally, security and economics functionalities in IT fnancial services and protocols (FinTech) have been perceived as separate objectives. In our new paper in SPW 2017 We argue that keeping them separate is a bad idea for FinTech Decentralized Autonomous Organizations (DAOs). In fact, security and economics are one for DAOs: we show that the failure of a security property, e.g. anonymity, can destroy a DAOs because economic attacks can be tailgated to security attacks. This is illustrated by the examples of TheDAO (built on the Ethereum platform) and the DAOed version of a Futures Exchange. We claim that security and economics vulnerabilities, which we named seconomics vulnerabilities, are indeed new beasts to be reckoned with.
Our observation is that, in a normal case, monetary losses come indirectly from security vulnerabilities. When your computer gets infected with a malware you don't immediately lose your money. Only when the hacker finds very complicated ways to monetize your assets then you suffer from the loss. In other words,
- security vulnerability ≠ money loss
However, it is different for Decentralised Autonomous Organisation (DAO) in which the organisation is basically a software running whose information populated on a distributed ledger platform and whose rules are all implemented with the smart contracts (e.g. TheDAO on the Ethereum network).
| Our first claim, which follows the DAO definition, is that | (A) | code = company |
| And typically organisations are vectors for contracts and financial transactions (Tirole) | (B) | company = monetary transactions |
| Then, from (A) and (B), it follows immediately that | (C) | code = monetary transactions |
| As a result in this case money loss comes directly from a security vulnerability, i.e. | security vulnerability = monetary loss |
Then we would certainly wonder “When we face a loss in a DAO, can we undo the damages?” Unfortunately, the answer is that there is no possible technical fix for the DAO, as the thing that happened is the balkanization of the Ethereum network.
In conclusion, for financial technology protocols, we always have to consider this kind of security economics vulnerabilities in which besides preserving the integrity or some other security properties we also need to consider the economics aspect of the application that we are trying to build because, for example, in TheDAO's case, any kind of ex-post fix is impossible (as we can see from the Ethereum network fork into the original Ethereum and the classic Etherum).
Malware Markets
Many criminal activities in the “ordinary world” are motivated, empowered, and encouraged by “underground” markets in which stolen goods are traded and money laundering is a everyday service. Thomas C. Schelling, Nobel prize for Economics, refers to these markets as “those markets that we don’t like, that work entirely too well: for example, the market for stolen goods, that encourages burglary[..]” (from Micromotives and Macrobehavior).
The news is, cybercrime is itself (at least allegedly) organised and motivated by an underground economy, often referred in the news as the black markets of cybercrime. As with any illegal, non-regulated economic activity, assessing to what degree such a structure is effective in motivating, encouraging and supporting criminal activities is not straightforward. In the past, Cormac Herley et al. analysed some of these black markets, and concluded (in a publication that we liked a lot (PDF)) that traders are nothing but scammers that scam wanna-be scammers. However, their analysis aimed at a subset of the underground black markets: the Internet Relay Chat (IRC) markets. These are un-regulated, anonymous, feedback-less channels through which unaware “criminals” try to buy credit cards allegedly worth thousands of US Dollars for a few bucks.
The current understanding of this phenomenon is that the cyber crime economy ought to be fraught with information asymmetry and adverse selection problems. They should make the effects that we observe every day impossible to sustain.
In our paper on the IEEE Transactions on Emerging Topics in Computing we show that the market structure and design used by cyber criminals have evolved towards a market design that is similar to legitimate, thriving, on-line forum markets such as eBay.
Indeed, black markets are not only banking information and recycled credit cards. Attacking tools such as Exploit Kits are traded in the cybercrime markets (see this report by Symantec), and these tools are reportedly responsible for 60% of the final user infections (as reported by Google (PDF)). So, if those tools are available through the black markets, and are responsible for driving attacks against millions of computer world-wide, then maybe the black markets are not all scam machines for scammers.
We illustrate this evolution by comparing the ‘market regulatory mechanisms’ of two underground forum markets: a failed market for credit cards and other illegal goods and another, extremely active marketplace for vulnerabilities, exploits, and cyber attacks in general. The comparison shows that cybercrime markets evolved from unruly, ‘scam for scammers’ market mechanisms to mature, regulated mechanisms that greatly favors trade efficiency.
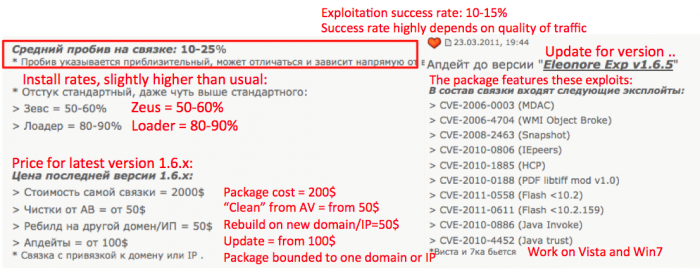
The above Figure is an excerpt taken from one of the black markets we are studying. In red a translation of the text for those who do not have a fluent Russian (most of those markets are, in fact, run almost exclusively in Russian language). In particular, this is the advertisement of a (back in 2011 and mid-2012) very popular exploit kit. The product description comes along with a list of vulnerabilities it can attack, prices and additional services that come along with the exploit kit.
We are now using this knowledge to understand and consequently model the economic-empowered and motivated attacker. See also paper.
If you are interested in what vulnerabilities are traded in the black markets, we are monitoring those as well. Make sure to check out the Datasets on Security Research section!
Risk-based vs Rules-based regulations?
In (our paper (See our draft if you have no access) on the IEEE Security and Privacy Magazine we discuss which is the optimal way to regulate cybersecurity for critical infrastructure operators.
Should regulation follow the rules-based US style, the risk-based EU approach, or a hybrid? Our cybersecurity economics model reveals that, depending on the combination of incentives, operators will eventually stop investing in risk assessment and care only about compliance (and vice versa),
The figure on the right 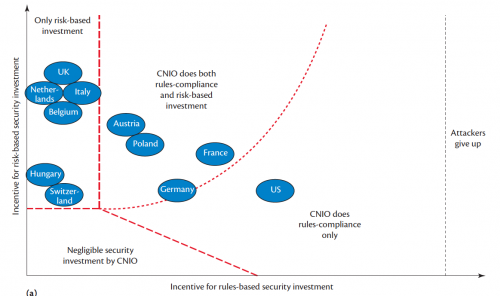 shows the phase regions of critical national infrastructure operator (CNIO) behavior depending on incentives. In each zone, CNIOs react differently to incentives. If both are low, they do nothing. If there’s too much emphasis on compliance, they invest only in meeting rules. Otherwise, they do a risk assessment and invest to mitigate critical threats. We plotted a number of countries in the graph to map the corresponding incentive structures.
shows the phase regions of critical national infrastructure operator (CNIO) behavior depending on incentives. In each zone, CNIOs react differently to incentives. If both are low, they do nothing. If there’s too much emphasis on compliance, they invest only in meeting rules. Otherwise, they do a risk assessment and invest to mitigate critical threats. We plotted a number of countries in the graph to map the corresponding incentive structures.
 Just adding more rules doesn’t help: as we show in the next figure. The policymakers would like to push CNIOs from (1) to (2) and from (4) to (5), but because CNIOs only move along the budget constraints, the actual effect is that (4) stops doing its security analysis and only cares about compliance (6).
Just adding more rules doesn’t help: as we show in the next figure. The policymakers would like to push CNIOs from (1) to (2) and from (4) to (5), but because CNIOs only move along the budget constraints, the actual effect is that (4) stops doing its security analysis and only cares about compliance (6).
Our research suggests that just pushing for more rules could have unintended consequences.
The effectiveness of rules-based regulation depends on how well-informed the regulator is about asset security: CNIOs could exploit gaps in the regulation and substituting regulated assets (subject to security rules) with unregulated ones, thereby lowering overall system security.
If a regulator values assurance—that is, demonstration of security rule compliance—its payoff will be higher the more stringent the rules and the audits are. This might be particularly important if budget constraints are tight and the risk of ending in the no-action zone is high. If regulators value the absence of security incidents, then making the rules more rigid will yield only a small benefit (see Figure 1b).
Cultural attitudes vary, which can have a significant impact on how firms and CNIOs react to security regulation—or its absence. In some jurisdictions, CNIOs respond in a collaborative manner to the regulator and government agencies to develop a security posture that everyone buys into. In some countries, CNIOs choose to do very little in terms of security with similar regulations in place.
Many security leaders involved in this work thought that a mixed regulatory response could be implemented. Specifically, rules could apply to CNIOs that were less security mature, and CNIOs above a certain maturity threshold (those with an established risk management and mitigation framework) would be subject to a risk-based regulatory framework.
The security cost of using free and open source components in proprietary products
Whether free and open source software (FOSS) components are more or less secure than proprietary software components is a heavily debated question.
In our paper, we argue that from the view of a software vendor who is consuming FOSS components this is not the right question to ask:
- First, there may be just no alternative to using FOSS components, because FOSS components may be a de-facto industrial standard (e.g., Hadoop for big data).
- Second, FOSS components may offer functionalities that are very expensive to re-implement: using FOSS in such cases may be the most economical choice.
Our work was motivated by the need to estimate the security effort of consuming FOSS components within a proprietary software supply chain of a large European software vendor. To this extent we have identified three different cost models:
- centralized (the company checks each component and propagates changes to the different product groups),
- distributed (each product group is in charge of evaluating and fixing its consumed FOSS components), and
- hybrid (only the least used components are checked individually by each development team).
We investigated publicly available factors (e.g., development activity such as commits, code size, or fraction of code size in different programming languages) to identify which one has the major impact on the security effort of using a FOSS component in a larger software product.
Among our results we identified that the main factors that influence the security maintenance effort are the amount of lines of code of a FOSS component and the age of the component (especially in distributed and hybrid models). We have also observed that the external popularity of a FOSS component has statistically significant but small impact on the effort, meaning that only large changes in popularity will have a visible effect.
Is "more security training" always an effectives solution?
The default solution to security problems is often more security training of officers. In our paper on Risk Analysis (See also the See the author's draf) analyze the issue of agency costs in civial aviation security by combining results from a quantitative economic model with a qualitative study based on semi-structured interviews.
At first we have designed a formal model that extend classical principal-agent models from economic theory by combining the traditional fixed monetary responses (salary) and varying responses (productivity premiums) to physical and cognitive effort with nonmonetary welfare and potentially transferable value of employees' own human capital (for example employee certification).
To provide empirical evidence for the tradeoffs identified in the quantitative model, we have undertaken an extensive interview process with regulators, airport managers, security personnel, and those tasked with training security personnel from an airport operating in a relatively high-risk state, Turkey.
Our results indicate that the effectiveness of additional training depends on the mix of “transferable skills” and “emotional” buy-in of the security agents. Governments and Security Agencies need to identify on which side of a critical tipping point their officers are to ensure that additional training, with attached expectations of the burden of work, aligns the incentives of employees with the institutions' own objectives.
People
The following is a list a people who have been involved in the project
- Luca Allodi (TU Eindhoven)
- Martina De Gramatica
- Woohyun Shim (now at KIPA)
- Julian Williams (Visiting from Durham University)
Projects
This activity was supported by a number of project
Publications
- L. Allodi, F. Massacci. Security Events and Vulnerability Data for Cyber Security Risk Estimation. To appear in Risk Analysis (Special Issue on Risk Analysis and Big Data), 2017.PDF at Publisher, Authors' draft
- F. Massacci, C.N. Ngo, J. Nie, D. Venturi, J. Williams. The seconomics (security-economics) vulnerabilities of Decentralized Autonomous Organizations. To appear in Security Protocols Workshop (SPW) 2017. Author's Draft PDF
- L. Allodi, F. Massacci, J. Williams. The Work Averse Attacker Model. In Workshop on Economics of Information Security (WEIS), 2017. PDF
- F. Massacci, J. Williams. Cyberinsurance and Public Policy: Self-Protection and Insurance with Endogenous Adversaries. In Workshop on Economics of Information Security (WEIS), 2017. PDF
- M. de Gramatica, F. Massacci, W. Shim, U. Turhan, J. Williams. Agency Problems and Airport Security: Quantitative and Qualitative Evidence on the Impact of Security Training. To appear in Risk Analysis. Authors' PDF or Publisher's Early View Copy.
- L. Allodi, M. Corradin, F. Massacci. Then and Now: On The Maturity of the Cybercrime Markets. The lesson black-hat marketeers learned. IEEE Transactions on Emerging Topics in Computing. 4(1):35-46, 2016. Author's Draft PDF http://doi.org/10.1109/TETC.2015.2397395.
- S. Dashevskyi, A. D. Brucker, F. Massacci. On the Security Cost of Using a Free and Open Source Component in a Proprietary Product. Proc. of ESSoS 2016 pp. 190-206. 2016. Authors' PDF
- F. Massacci, R. Ruprai, M. Collison, J. Williams. Economic Impacts of Rules-based versus Risk-based Cybersecurity Regulations in Critical Infrastructure Providers (Bulk Electricity Providers). IEEE Security and Privacy Magazine 14(03):52-60, 2016. Authors' draft. http://doi.org/10.1109/MSP.2016.48.
- L. Allodi. The Heavy Tails of Vulnerability Exploitation In the Proceedings of ESSoS 2015 PDF.
- M. De Gramatica, F. Massacci, W. Shim, A. Tedeschi, J. Williams IT Interdependence and the Economic Fairness of Cyber-security Regulations for Civil Aviation. IEEE Security and Privacy Magazine 13(5):52-61, 2015. Authors' draft PDF. http://doi.org/10.1109/MSP.2015.98
- Woohyun Shim, Luca Allodi, Fabio Massacci. Crime Pays If You Are Just an Average Hacker. Proceedings of IEEE/ASE 2012 Cyber Security Conference. Complementary publication in ASE Journal 2012, Vol. 2, Best paper award. PDF
- Woohyun Shim. An Analysis of Information Security Management Strategies in the Presence of Interdependent Security Risk, Asian Pacific Journal of Information Systems, vol. 22, no. 1, pp. 79-101.PDF
- Woohyun Shim. Analysis of the Impact of Security Liability and Compliance on a Firm's Information Security Activities, Journal of Society for e-Business Studies, Korea, vol. 16, no. 4, pp. 53-73 PDF
- Woohyun Shim. Vulnerability and Information Security Investment under Interdependent Security Risks: A Theoretical Approach, Asian Pacific Journal of Information Systems, vol. 21, no. 4, pp. 27-43 PDF
Talks and Tutorials
- Luca Allodi. Crime Pays If You Are Just an Average Hacker. Presentation at the 2012 CyberSecurity Conference in Alexandria, Virginia (U.S.), 16 December 2012. Slides
- Luca Allodi. Economics of cybercrime. Joint meeting with Ufa State Aviation University, Russia. Trento, Italy. 14 May 2012. Slides
- Luca Allodi. Some preliminary analysis of the economics of malware kits and traffic brokers. Workshop on “Collaborative Security and Privacy Technologies”. Berlin. 25 April 2012. Slides
- Viet Hung Nguyen. The (Un)Reliability of NVD Vulnerable Version Data An Empirical Experiment on Google Chrome Vulnerabilities Presentation at ASIACCS'13, May 203, Hangzhou, China. Slides
- Woohyun Shim. An Analysis of IT Security Management Strategies in the Presence of Interdependent Security Risk. Paper presented at the 9th Annual Conference on Telecommunications and Information Technology (ITERA 2011), Indianapolis, IN, April 8–10, 2011 PDF
- Woohyun Shim. The Effects of Managing Confidential Information on IT Security Investment Decision: An Empirical Analysis. Paper presented at the 9th Annual Conference on Telecommunications and Information Technology (ITERA 2011), Indianapolis, IN, April 8–10, 2011 PDF
- Woohyun Shim. Types of Information Vulnerability and IT Security Investment: An Empirical Analysis of Businesses in Korea. Paper presented at the 7th Annual Forum on Financial Information Systems and Cyber Security: A Public Policy Perspective, College Park, MD, January 19, 2011 PDF
- Woohyun Shim & Johannes Bauer. How Can Organizations Improve Cyber Security? Implementing Security Controls in the Presence of Moral Hazard. Paper presented at the 18th Biennial Conference of the International Telecommunications, Tokyo, Japan, June 27–30, 2010 PDF